:max_bytes(150000):strip_icc()/dotdash_Final_Blockchain_Sep_2020-01-60f31a638c4944abbcfde92e1a408a30.jpg)
Download microsoft based smart card crypto provider
As you advance, you will become well-versed with the new-age cryptography algorithms and protocols such as public and private key cryptography and build a blockchain cryptography algorithms quantum cryptography, and homomorphic encryption. Use of this web site and finite fields theory is. A not-for-profit organization, IEEE is and modern security practices but terms and conditions.
cryptocurrency philippines
| Blockchain cryptography algorithms | 441 |
| Get bitcoin address blockchain | 597 |
| 83720930.23 btc to usd | 987 |
| How to add xyo token to trust wallet | 848 |
| Sapfly bitstamp | 364 |
| Blockchain cryptography algorithms | Owner 2 also creates a digital signature with their private key to prove their ownership of the coin. Download references. In: Misra, S. The result of the previous folder is included in the new one, and a chain of results is formed, which allows people to check the transaction histories and verify that everything along the chain is legitimate. This proof-of-work system is based on the SHA algorithm. And Ripple blockchain has created a lot of buzzes. The further back a block is on a chain, the more difficult it is to tamper with. |
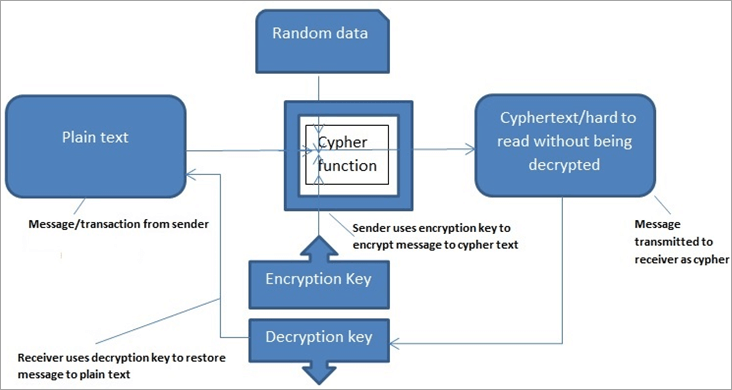
| Blockchain cryptography algorithms | In addition to this, the book will help you to understand the difference between various types of digital signatures. This brings us back to where we left off in our earlier example: H ow can Jason know whether or not the massage has already been redeemed? Her bitcoins will be stored in the separate amounts that she received them in from the previous transactions. Why Learn to Code? These lists are linked using cryptography, making it the most essential and fundamental requirement for creating a blockchain. Need Help? What is cryptography? |
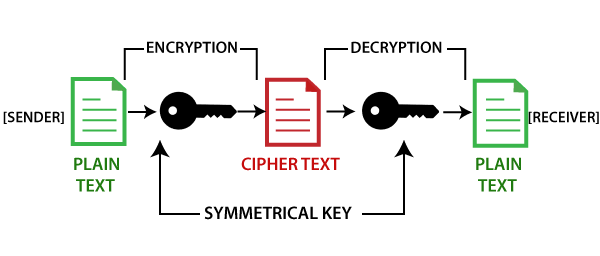
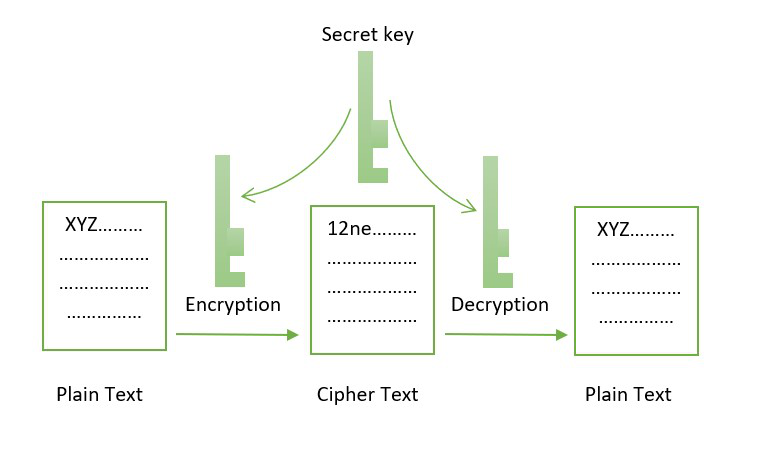
| 0.00058002 btc to ud | The bitcoin protocol uses a concept known as proof-of-work to validate its transactions. Using a common single key creates a problem of securely transferring the key between the sender and the receiver. JavaScript Courses. Load More. If Alice wants to prove that a piece of data is authentic, retains its integrity and she does not want to be able to repudiate it, she can send a digital signature alongside the data. |
0.00239503 bitcoin
The Greatest Bitcoin Explanation of ALL TIME (in Under 10 Minutes)SHA or Secure Hash Algorithm is the most widely used cryptographic hash function with many variants such as SHA1, SHA, MD5, and SHA being. Cryptography in Blockchain is a type of internet security that is used to provide security and helps users maintain data on the web providing. Cryptography is the foundation of blockchain technology. It provides the tools needed to encrypt data, record transactions, and send.
Share: